Explanation
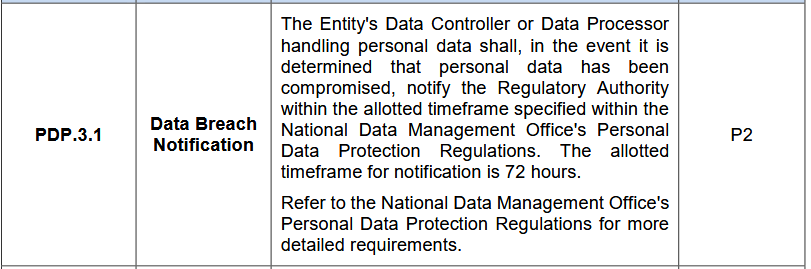
In case an organization’s personal data is compromised (i.e., exposed, stolen, or leaked), the responsible party—either the Data Controller or Data Processor—must inform the Regulatory Authority. This notification must happen within a strict 72-hour window, in line with the requirements laid out by the National Data Management Office (NDMO) under their Personal Data Protection Regulations. This approach aligns with NDMO regulations and ensures compliance while safeguarding personal data.
Key Points
- Data Breach Definition: A breach occurs when unauthorized access, disclosure, or destruction of personal data happens.
- Data Controller/Processor Responsibility: The Data Controller or Processor managing personal data is responsible for notifying the appropriate authorities.
- 72-Hour Notification Window: Once the breach is discovered, the responsible entity has 72 hours to notify the Regulatory Authority.
- Contents of Notification: The breach notification should include details of the breach, the scope, the impact on individuals, and the corrective actions taken.
- Regulatory Compliance: The notification must meet the National Data Management Office (NDMO) Personal Data Protection Regulations’ specific requirements.
- Penalties for Non-Compliance: Failing to notify within the required timeframe may lead to fines and penalties under the regulatory framework.
General Activation Steps
- Identify the Breach: Detect and confirm the breach, evaluate its severity, and gather relevant details.
- Assess the Impact: Determine the scope and individuals affected by the breach (what data was compromised and how many data subjects are involved).
- Prepare the Notification:
- Description of the breach (what happened, how it was detected).
- Data Impacted: Detail of personal data affected.
- Mitigation Measures: Steps being taken to address and prevent further impact.
- Contact Details: Include details of the individual or team responsible for managing the breach.
- Submit the Notification to the Regulatory Authority within 72 hours.
- Notify Impacted Individuals (if applicable): After notifying the authority, inform the affected individuals, especially if the breach can cause harm (e.g., identity theft).
- Update Internal Documentation: Record the incident, corrective actions, and results for auditing and future references.
Use Cases
- Financial Institutions: A bank detects unauthorized access to customer accounts, compromising personal and financial information.
- Healthcare Providers: A hospital experiences a ransomware attack that exposes patient medical records.
- E-Commerce Companies: A data breach of customer profiles, including email and payment information, occurs due to a vulnerability in the system.
Dependencies
- Incident Response Team: Ensure an active and well-trained team to handle breaches swiftly.
- Data Governance Policies: An established data governance framework ensures the breach process is well-managed.
- Technology Monitoring Tools: Implement monitoring and detection tools to discover breaches early.
- Legal and Regulatory Advisors: Have access to legal guidance for compliance with specific regulations.
- Employee Training: Regular security awareness training is essential for early detection and proper handling of breaches.
Tools and Technologies
- Security Information and Event Management (SIEM): Tools like Splunk, IBM QRadar, or LogRhythm to detect and monitor breaches.
- Incident Management Platforms: JIRA, ServiceNow, or similar systems to track the breach and manage the response workflow.
- Encryption and Data Masking Tools: Tools such as Vormetric, Talend, or Oracle Advanced Security for mitigating the impact of data breaches.
- Endpoint Detection and Response (EDR): Tools like CrowdStrike, Microsoft Defender for Endpoint to detect and isolate breaches at endpoint levels.
- Notification Tools: Use compliance management platforms to assist with breach notifications, like OneTrust or TrustArc.
For Your Further Reading:
- Data Strategy vs. Data Platform Strategy
- KSA PDPL – Initial Framework
- KSA PDPL – Consent Not Mandatory
- KSA PDPL – Article 5, Article 6, Article 7, & Article 8, Article 9
- KSA NDMO – Data Catalog and Metadata
- KSA NDMO – Personal Data Protection – Initial Assessment
- KSA NDMO – Classification Process – Data Classification Metadata
- KSA NDMO – DG Artifacts Control – Data Management Issue Tracking Register
- KSA NDMO – Personal Data Protection – PDP Plan, & PDP Training
- Enterprise Architecture Governance & TOGAF – Components
- Enterprise Architecture & Architecture Framework
- TOGAF – ADM (Architecture Development Method) vs. Enterprise Continuum
- TOGAF – Architecture Content Framework
- TOGAF – ADM Features & Phases
- Data Security Standards
- Data Steward – Stewardship Activities
- Data Modeling – Metrics and Checklist
- How to Measure the Value of Data
- What is Content and Content Management?

