Explanation
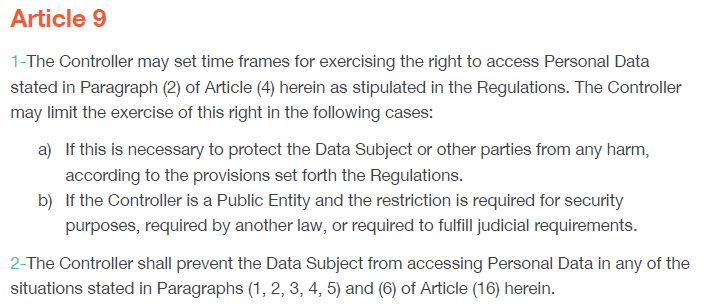
Article 9 of the KSA PDPL allows the Controller (the entity handling personal data) to set timeframes for when individuals (Data Subjects) can access their personal data. It also provides conditions under which the Controller may limit access, particularly when it’s necessary to prevent harm or when the Controller is a public entity dealing with security, legal, or judicial matters.
By defining clear timeframes and conditions for data access, the Controller ensures a balance between the Data Subject’s rights and legal, security, or harm-prevention concerns.
Key Points
- Timeframes for Access: The Controller can establish deadlines or schedules for responding to requests to access personal data.
- Access Limitations: The Controller can restrict access if:
- It’s necessary to protect the Data Subject or others from harm.
- The Controller is a public entity and access limitations are required for security, legal, or judicial reasons.
- Prevention of Access: The Controller can entirely prevent access under specific circumstances outlined in the regulations.
General Activation Steps
- Define Timeframes: Establish clear time limits for data access requests, ensuring these are compliant with regulatory guidelines.
- Set Criteria for Limitation: Identify situations where access should be limited to prevent harm or comply with security and legal requirements.
- Notify Data Subjects: Ensure Data Subjects are informed about timeframes and any potential limitations when requesting access to their personal data.
- Document Policies: Create a policy outlining how and when access may be restricted, with clear guidelines for employees handling these requests.
Use Cases
- Protection from Harm: If accessing personal data could lead to physical or emotional harm, the Controller can restrict access. For example, in cases involving domestic abuse, accessing certain data might endanger someone.
- Public Entity & Security: A government agency may deny access to certain personal data if releasing it poses a national security risk or violates other laws.
- Judicial Requirements: In an ongoing legal investigation, certain personal data might be restricted to preserve the integrity of the investigation.
Dependencies
- Regulatory Guidelines: The Controller must adhere to the detailed regulations provided under the law, which will clarify the conditions and timeframes for limiting access.
- Legal Compliance: Ensure that any access limitations comply with other national laws, especially when dealing with public security or judicial matters.
- Risk Assessment: A solid process must be in place to evaluate the risk of harm before restricting access to personal data.
Tools/Technologies
- Data Management Platforms: Implement systems to manage access requests efficiently (e.g., access tracking tools).
- Audit and Monitoring Tools: Use tools that log access to personal data, including restrictions, to ensure compliance.
- Security and Risk Management Tools: Deploy risk assessment and data classification tools to evaluate the potential harm before allowing or restricting data access.
- Legal and Compliance Solutions: Utilize tools that provide real-time updates on legal changes or security requirements that may affect data access.
For Your Further Reading:
- Data Strategy vs. Data Platform Strategy
- KSA PDPL – Initial Framework
- KSA PDPL – Consent Not Mandatory
- KSA PDPL – Article 5, Article 6, Article 7, & Article 8
- KSA NDMO – Data Catalog and Metadata
- KSA NDMO – Personal Data Protection – Initial Assessment
- KSA NDMO – Classification Process – Data Classification Metadata
- KSA NDMO – DG Artifacts Control – Data Management Issue Tracking Register
- KSA NDMO – Personal Data Protection – PDP Plan, & PDP Training
- Enterprise Architecture Governance & TOGAF – Components
- Enterprise Architecture & Architecture Framework
- TOGAF – ADM (Architecture Development Method) vs. Enterprise Continuum
- TOGAF – Architecture Content Framework
- TOGAF – ADM Features & Phases
- Data Security Standards
- Data Steward – Stewardship Activities
- Data Modeling – Metrics and Checklist
- How to Measure the Value of Data
- What is Content and Content Management?

