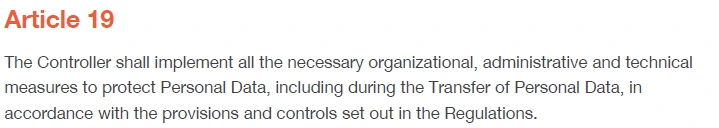
Abstract Of KSA PDPL – Article 19
This paper provides an in-depth analysis of Article 19 of the Kingdom of Saudi Arabia’s Personal Data Protection Law (PDPL), focusing on the necessary organizational, administrative, and technical measures for ensuring the security of personal data during its transfer. The research delves into the strategic requirements and practical implementation steps for controllers to protect data while complying with regulatory provisions. Additionally, key challenges and risks, methodologies for applying these measures, relevant tools and technologies, and real-world use cases are explored.
Introduction Of KSA PDPL – Article 19
With the increasing global emphasis on data privacy and protection, the Kingdom of Saudi Arabia introduced the PDPL to safeguard personal data in compliance with international best practices. Article 19 of the law emphasizes the implementation of necessary organizational, administrative, and technical measures during the transfer of personal data. Ensuring the secure transfer of data is critical as breaches during data transmission can lead to severe consequences, including regulatory penalties and reputational damage. This paper explores the essential measures stipulated by Article 19, offering guidelines on how organizations can ensure compliance with the law while minimizing risks.
Key Words
Personal Data Protection; PDPL; Article 19; Data Transfer; Security Measures; Organizational Measures; Administrative Measures; Technical Measures; Data Compliance; Saudi Arabia; Data Privacy Law
Explanation of KSA PDPL – Article 19
Article 19 of the PDPL mandates that organizations (Controllers) put in place comprehensive strategies to protect personal data, even when it is being transferred. These strategies must cover organizational practices, administrative oversight, and the application of technical safeguards. The goal is to ensure personal data is not exposed to unauthorized access, breaches, or misuse, especially during transfer processes, which are often vulnerable to attacks.
Key Strategic Points
- Organizational Measures: Establishment of governance frameworks, including roles and responsibilities, to oversee data protection efforts especially during data transfers.
- Administrative Measures: Development of policies and procedures that dictate how personal data should be handled, processed, and transferred securely.
- Technical Measures: Implementation of encryption, secure transfer protocols, and continuous monitoring tools to ensure the safe movement of data between systems.
- Compliance Monitoring: Regular audits and assessments to ensure the effectiveness of the implemented measures and alignment with PDPL requirements.
- Incident Response: Creation of a comprehensive incident response plan to quickly react to any breach or vulnerability during the transfer process.
General Activation Steps
- Conduct a risk assessment to identify vulnerabilities in the data transfer processes.
- Develop comprehensive policies governing the transfer of personal data, ensuring compliance with Article 19.
- Implement technical safeguards such as encryption and secure communication protocols.
- Establish data governance structures, assigning responsibilities to data protection officers or equivalent roles.
- Create a robust monitoring system to continuously oversee the integrity of data during transfers.
- Ensure periodic staff training to align organizational knowledge with best practices in data protection.
- Regularly perform audits and reviews to ensure adherence to legal and organizational policies.
- Develop an incident response plan for immediate action in case of data breaches or unauthorized access.
Methodology
To fulfill the requirements of Article 19, a multi-step approach should be adopted:
- Risk-Based Approach: Conduct a comprehensive assessment of risks associated with data transfer, identifying critical points of vulnerability.
- Policy Development: Draft and implement policies that define clear guidelines for the transfer of personal data, including acceptable methods, authorized personnel, and restrictions.
- Technical Implementation: Utilize encryption, secure communication channels (e.g., VPNs, TLS/SSL), and data loss prevention (DLP) tools.
- Training and Awareness: Conduct training for all personnel involved in data handling and transfer processes to ensure compliance with the law and organizational procedures.
- Continuous Monitoring and Audits: Use tools and protocols that continuously track the data being transferred, triggering alerts for any anomalies or breaches.
- Incident Response Plan: Develop a predefined response plan to address potential breaches or security issues during transfers.
Use Cases
- International Data Transfers: Organizations transferring personal data to entities outside of Saudi Arabia must ensure compliance with Article 19 by utilizing appropriate technical safeguards such as encryption and ensuring contractual clauses that bind the recipient to the same security standards.
- Data Sharing with Third-Party Vendors: Controllers working with third-party vendors (e.g., cloud service providers) must ensure that these vendors have implemented adequate organizational and technical measures to protect personal data.
- Cross-Departmental Data Transfers: Within large organizations, personal data is often transferred between departments. Internal procedures must be developed to ensure data is transferred securely and in compliance with organizational policies.
Dependencies
- Legal and Regulatory Guidelines: Adherence to PDPL and other applicable laws, including international regulations such as GDPR for cross-border transfers.
- Technological Infrastructure: Availability of secure communication channels and encryption technologies for protecting data during transfer.
- Qualified Personnel: The need for trained personnel who understand data privacy and security regulations, including data protection officers and IT specialists.
- Third-Party Contracts: Proper agreements in place with third-party processors to ensure their compliance with data protection standards.
Tools/Technologies
- Encryption Technologies: AES (Advanced Encryption Standard), RSA encryption for data in transit.
- Secure Transfer Protocols: TLS (Transport Layer Security), SSH (Secure Shell), VPNs (Virtual Private Networks).
- Data Loss Prevention (DLP) Systems: Tools for monitoring and protecting data during transfer.
- Monitoring and Logging Tools: Systems that track data flows and detect anomalies or unauthorized access.
- Incident Response Platforms: Tools that assist in quickly identifying and mitigating breaches during transfers.
Challenges & Risks in KSA PDPL – Article 19
- Cybersecurity Threats: Data transfer processes are vulnerable to interception by cybercriminals if adequate security measures are not implemented.
- Third-Party Risks: Ensuring that third-party vendors adhere to the same data protection standards can be challenging.
- Human Error: Lack of proper training or accidental disclosure during transfer processes may lead to breaches.
- Technological Gaps: Outdated or insufficient encryption and transfer protocols can expose organizations to risks.
- Compliance Complexity: Aligning both national and international regulatory requirements during data transfers can be complicated, especially for organizations that operate across borders.
Conclusion
Article 19 of the KSA PDPL imposes critical responsibilities on Controllers to ensure the protection of personal data during transfers. Organizations must implement a combination of organizational, administrative, and technical measures to secure data throughout its movement. By conducting comprehensive risk assessments, establishing secure transfer protocols, and adhering to regulatory compliance, organizations can safeguard personal data and mitigate the risks of breaches or unauthorized access.
References
- KSA PDPL, and NDMO
- National Cybersecurity Authority (NCA). (2021). Cybersecurity Regulations for Data Protection.
- European Union. (2018). General Data Protection Regulation (GDPR).
- International Association of Privacy Professionals (IAPP). (2022). Best Practices in Data Transfer Security.
For Your Further Reading:
- Big Data vs. Traditional Data, Data Warehousing, AI, and Beyond
- Big Data Security, Privacy, and Protection, & Addressing the Challenges of Big Data
- Data Strategy vs. Data Platform Strategy
- ABAC – Attribute-Based Access Control
- Consequences of Personal Data Breaches
- KSA PDPL (Personal Data Protection Law) – Initial Framework
- KSA PDPL – Consent Not Mandatory
- KSA PDPL Article 4, Article 5, Article 6, Article 7, Article 8, Article 9, & Article 10
- KSA PDPL Article 11, Article 12, Article 13, Article 14, Article 15, Article 16, Article 17, & Article 18
- KSA NDMO – Data Catalog and Metadata
- KSA NDMO – Personal Data Protection – Initial Assessment
- KSA NDMO – DG Artifacts Control – Data Management Issue Tracking Register
- KSA NDMO – Personal Data Protection – PDP Plan, & PDP Training, Data Breach Notification
- KSA NDMO – Classification Process, Data Breach Management, & Data Subject Rights
- KSA NDMO – Privacy Notice and Consent Management
- Enterprise Architecture Governance & TOGAF – Components
- Enterprise Architecture & Architecture Framework
- TOGAF – ADM (Architecture Development Method) vs. Enterprise Continuum
- TOGAF – Architecture Content Framework
- TOGAF – ADM Features & Phases
- Data Security Standards
- Data Steward – Stewardship Activities
- Data Modeling – Metrics and Checklist
- How to Measure the Value of Data
- What is Content and Content Management?


